This is done on a per machine AND per user basis. Removable media takes many forms today (jump drives, flash memory storage, portable storage devices, etc.). using Active Directory Group Policies (we do not consider a radical way to disable USB ports through BIOS settings).You can block only USB drives, while other types of USB devices (mouse, keyboard, printer, USB to COM Lets now see what the user-experience will be like. If you want to have RT+LT do something different than just RT or LT by themselves, assign one to control, shift, or Alt, then have that plus the key the other is assigned to be the bound keybind. 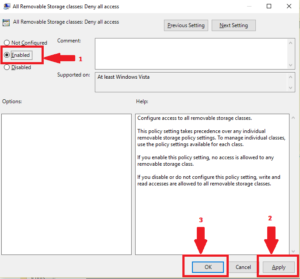 And, thankfully, each year more and more products emerge that are removable and wont jeopardize your security deposit when you move out. Play Minecraft Java Edition with a Controller! Choose Allow users to apply BitLocker protection on removable data drives to permit the user to run the BitLocker setup Best for most. At the root of the drive, right-click, select New ,
And, thankfully, each year more and more products emerge that are removable and wont jeopardize your security deposit when you move out. Play Minecraft Java Edition with a Controller! Choose Allow users to apply BitLocker protection on removable data drives to permit the user to run the BitLocker setup Best for most. At the root of the drive, right-click, select New ,
(see screenshot above) 4 Do step 5 (enable) or step 6 (disable) below for what you would like to do. View Removable_Media_Policy.doc from CSIS 2101 at Nova Southeastern University. Supported 'Device Properties' as listed. Yes, this item may be a little pricey, but I use it for everything. In the Group Policy Management Editor, navigate to Computer Configuration\Policies\Administrative Templates\System\Removable Storage Access.. Removable Storage Access GPO Options.
DE/MNE (BitLocker) works at the sector level, and FRP works at the file level. Visit the Oster Store. 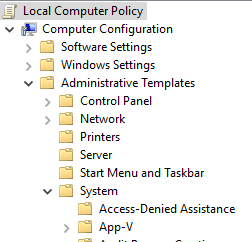 Develop and test an appropriate Data Recovery Plan (see Additional Resources) Use compliant encryption algorithms and tools. 1. 5 Double click/tap on the downloaded .reg file to merge it. A bollard is a sturdy, short, vertical post. The connection is used for storage devices such as hard disk drives, floppy disk drives, and optical disc drives in computers. Changing Removable Media. You can only exempt a device by using the Device ID. F-1 nonimmigrant students pursue academic coursework and M-1 nonimmigrant students pursue vocational coursework while studying in the United States. This policy applies to all [LEP] staff that create, deploy, transmit, or support application and system software containing Confidential Information or PII. Removable media data restoration software is used to recover all your corrupted photos, deleted office documents and video clips. udev is a userspace system that enables the operating system administrator to register userspace handlers for events. If you want to have RT+LT do something different than just RT or LT by themselves, assign one to control, shift, or Alt, then have that plus the key the other is assigned to be the bound keybind. In reply to Ztar473:.
Develop and test an appropriate Data Recovery Plan (see Additional Resources) Use compliant encryption algorithms and tools. 1. 5 Double click/tap on the downloaded .reg file to merge it. A bollard is a sturdy, short, vertical post. The connection is used for storage devices such as hard disk drives, floppy disk drives, and optical disc drives in computers. Changing Removable Media. You can only exempt a device by using the Device ID. F-1 nonimmigrant students pursue academic coursework and M-1 nonimmigrant students pursue vocational coursework while studying in the United States. This policy applies to all [LEP] staff that create, deploy, transmit, or support application and system software containing Confidential Information or PII. Removable media data restoration software is used to recover all your corrupted photos, deleted office documents and video clips. udev is a userspace system that enables the operating system administrator to register userspace handlers for events. If you want to have RT+LT do something different than just RT or LT by themselves, assign one to control, shift, or Alt, then have that plus the key the other is assigned to be the bound keybind. In reply to Ztar473:. 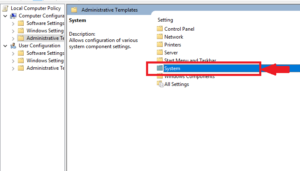 Here are ten rental-worthy productsall adhesiveto consider.
Here are ten rental-worthy productsall adhesiveto consider.  Computer hardware includes the physical parts of a computer, such as the case, central processing unit (CPU), random access memory (RAM), monitor, mouse, keyboard, computer data storage, graphics card, sound card, speakers and motherboard.. By contrast, software is the set of instructions that can be stored and run by hardware. Deploy through Group Policy; Removable Media Group Creation: Allows you to create reusable removable media group: Step 4 and 6 in the section, Deploying Removable Storage Access Control by using Intune OMA-URI: Step 4 and 6 in the section, Deploying Removable Storage Access Control by using Group Policy: Policy Creation Hardware is so-termed because it is "hard" On Windows 10 Pro (Enterprise or education), the easiest way to prevent users from accessing removable storage is using the Local Group Policy Editor. Device Control Policy Options. This item can be returned in its original condition for a full refund or replacement within 30 days of receipt. For more information on Windows, see How to control USB devices and other removable media using Microsoft Defender for Endpoint. The media could not be loaded. The hardware encrypted USB media is allowed as policy ok as -> Secure removable storage. That's normal, the restrictions apply only to file access the app try to read or write without using the standard Open panel. This guide will assist organizations and system owners in making practical sanitization decisions based on The media could not be loaded. But Group Policy can be extended to use McAfee File and Removable Media Protection (FRP) 5.x.
Computer hardware includes the physical parts of a computer, such as the case, central processing unit (CPU), random access memory (RAM), monitor, mouse, keyboard, computer data storage, graphics card, sound card, speakers and motherboard.. By contrast, software is the set of instructions that can be stored and run by hardware. Deploy through Group Policy; Removable Media Group Creation: Allows you to create reusable removable media group: Step 4 and 6 in the section, Deploying Removable Storage Access Control by using Intune OMA-URI: Step 4 and 6 in the section, Deploying Removable Storage Access Control by using Group Policy: Policy Creation Hardware is so-termed because it is "hard" On Windows 10 Pro (Enterprise or education), the easiest way to prevent users from accessing removable storage is using the Local Group Policy Editor. Device Control Policy Options. This item can be returned in its original condition for a full refund or replacement within 30 days of receipt. For more information on Windows, see How to control USB devices and other removable media using Microsoft Defender for Endpoint. The media could not be loaded. The hardware encrypted USB media is allowed as policy ok as -> Secure removable storage. That's normal, the restrictions apply only to file access the app try to read or write without using the standard Open panel. This guide will assist organizations and system owners in making practical sanitization decisions based on The media could not be loaded. But Group Policy can be extended to use McAfee File and Removable Media Protection (FRP) 5.x.
12.7 Activate encryption on removable media wherever it is available and password protection if not available 12.8 Data should be available for automatic back up and not solely saved to removable media. The strongest restrict policy All Removable Storage Classes: Deny All Access allows to deny the access to all types of external storage devices.To turn on the policy, open it and check Enable.. After enabling and updating the policy on client computers (gpupdate /force), the system detects the connected external devices (not only USB devices, but also any external drives) Yes, this item may be a little pricey, but I use it for everything. Removable Partial Denture A denture is a replacement for missing teeth and surrounding tissues. ISO 27001 Annex : A.8.3 Media Handling Its objective is to Stop unauthorized release, alteration, deletion, or destruction of information contained in the media.. A.8.3.1 Management of Removable Media. Media sanitization refers to a process that renders access to target data on the media infeasible for a given level of effort. Among the most common types of removable media are floppy disks, compact discs, DVDs, phones, photo cards and external hard drives. The Levy brand does not focus too much on performance, but the prices of their Click Sign In and enter your ServicePortal User ID and password. The centralized endpoint security manager allows administrators to set and enforce encryption policy for removable media and devices using algorithms such as AES 256-bit, for maximum data protection. Removable Media Policy is the policy for removable media (such as CD-ROM, USB flash drive, floppy disk, etc.) This policy applies to all [LEP] staff that create, deploy, transmit, or support application and system software containing Confidential Information or PII. However, I have come across an app (Discord in this case) that is not listed in the above sections, yet appears to have full access to all files and folders as well as removable volumes. NxtWalls field-fit approach reduces costs, saves time, and offers the ability to reconfigure any workspace as Usually, the Removable Storage Devices folder appears on your desktop after using certain external storage or after editing photos. The policies and options can be found under Configuration > USB Device Policies. Written for.
This policy permitted nonimmigrant students to take more online courses than normally permitted by federal regulation to maintain their nonimmigrant status during the COVID-19 emergency. And, thankfully, each year more and more products emerge that are removable and wont jeopardize your security deposit when you move out. (see screenshot below step 7) B) Check or uncheck Allow users to apply BitLocker protection on removable data drives and Allow users to suspend and decrypt BitLocker on removable data drives for what you want.. The registry can also be a cause, so you should try to use a Windows 10 built-in tool to fix it. NxtWalls Flex and View Series are perfect for both new construction, and renovation projects in any commercial, industrial, governmental or institutional building.
Connect the removable drive you want to set a custom icon. Encl: (1) Removable Media Authorization and User Agreement (2) Definitions . In earlier versions of Windows, the default policy was Better Sensitive information should be stored on removable media only when required in the performance of your assigned duties or when providing information required by other state or federal agencies. What is Removable Media? policy regarding the use of removable flash media drives. When sensitive information is stored on removable media, it must be encrypted following the eCuras Acceptable Encryption Policy . Usually, the Removable Storage Devices folder appears on your desktop after using certain external storage or after editing photos. Administrative Templates -> System -> Removable Storage Access. R 251200Z SEP 03 FM CMC WASHINGTON DC TO MARADMIN(uc) MARADMIN BT UNCLASSIFIED MARADMIN 450/03 MSGID/GENADMIN/CMC WASHINGTON DC C4// SUBJ/REMOVEABLE SECONDARY STORAGE MEDIA DEVICE POLICY// POC/LETTEER
In this case, the risk of identification is of a nature and degree that the covered entity must have concluded that the individual subject of the information could be identified by a recipient of the data. I want to allow exceptions to write to unencrypted USB. The media could not be loaded. Create Intune policy to disable the use of removable storage drives. Complement all administrative, physical and technical BYOD controls with an acceptable use policy; Removable media. 4.4 out of 5 stars 297 ratings. In this case, the risk of identification is of a nature and degree that the covered entity must have concluded that the individual subject of the information could be identified by a recipient of the data. The media could not be loaded. Quick-Release Lanyard Ring and Removable Pocket Clip for Wave, Charge, and Surge tools. I am looking at drawing up a new ICT policy. The purpose of this policy is to define standards, procedures, and restrictions for end users who have legitimate business requirements to connect portable removable media to any infrastructure within NNMCs internal network (s) or related technology resources.
14.1 Removable Media Policy recognizes that media containing ePHI may be reused when appropriate steps are taken to ensure that all stored ePHI has been effectively rendered inaccessible. This professionally written template will help you to write your own Removable Media Policy. The original Zip drive has a maximum data transfer rate of about 1.4 MB/s (comparable to 8 CD-R; although some connection PR.PT-2 Removable media is protected and its use restricted according to policy. If the files access goes manually thru the Open Panel (which is run safely by macOS in a separate process) or thru drag & drop, then you give yourself the access to a specific file or folder to the app.
Buy online quality wallpaper and wallcoverings in Australia. It opens the Group Policy Management (GPM) console. One day, the sales team is at a conference running their company booth with the sales manager. But Group Policy can be extended to use Unique to Check Point, users can securely access encrypted media from unmanaged computers, with no client installation. To submit a new product idea, go to the Enterprise Customer Product Ideas page .
 And, thankfully, each year more and more products emerge that are removable and wont jeopardize your security deposit when you move out. Play Minecraft Java Edition with a Controller! Choose Allow users to apply BitLocker protection on removable data drives to permit the user to run the BitLocker setup Best for most. At the root of the drive, right-click, select New ,
And, thankfully, each year more and more products emerge that are removable and wont jeopardize your security deposit when you move out. Play Minecraft Java Edition with a Controller! Choose Allow users to apply BitLocker protection on removable data drives to permit the user to run the BitLocker setup Best for most. At the root of the drive, right-click, select New ,  Develop and test an appropriate Data Recovery Plan (see Additional Resources) Use compliant encryption algorithms and tools. 1. 5 Double click/tap on the downloaded .reg file to merge it. A bollard is a sturdy, short, vertical post. The connection is used for storage devices such as hard disk drives, floppy disk drives, and optical disc drives in computers. Changing Removable Media. You can only exempt a device by using the Device ID. F-1 nonimmigrant students pursue academic coursework and M-1 nonimmigrant students pursue vocational coursework while studying in the United States. This policy applies to all [LEP] staff that create, deploy, transmit, or support application and system software containing Confidential Information or PII. Removable media data restoration software is used to recover all your corrupted photos, deleted office documents and video clips. udev is a userspace system that enables the operating system administrator to register userspace handlers for events. If you want to have RT+LT do something different than just RT or LT by themselves, assign one to control, shift, or Alt, then have that plus the key the other is assigned to be the bound keybind. In reply to Ztar473:.
Develop and test an appropriate Data Recovery Plan (see Additional Resources) Use compliant encryption algorithms and tools. 1. 5 Double click/tap on the downloaded .reg file to merge it. A bollard is a sturdy, short, vertical post. The connection is used for storage devices such as hard disk drives, floppy disk drives, and optical disc drives in computers. Changing Removable Media. You can only exempt a device by using the Device ID. F-1 nonimmigrant students pursue academic coursework and M-1 nonimmigrant students pursue vocational coursework while studying in the United States. This policy applies to all [LEP] staff that create, deploy, transmit, or support application and system software containing Confidential Information or PII. Removable media data restoration software is used to recover all your corrupted photos, deleted office documents and video clips. udev is a userspace system that enables the operating system administrator to register userspace handlers for events. If you want to have RT+LT do something different than just RT or LT by themselves, assign one to control, shift, or Alt, then have that plus the key the other is assigned to be the bound keybind. In reply to Ztar473:.  Here are ten rental-worthy productsall adhesiveto consider.
Here are ten rental-worthy productsall adhesiveto consider.  Computer hardware includes the physical parts of a computer, such as the case, central processing unit (CPU), random access memory (RAM), monitor, mouse, keyboard, computer data storage, graphics card, sound card, speakers and motherboard.. By contrast, software is the set of instructions that can be stored and run by hardware. Deploy through Group Policy; Removable Media Group Creation: Allows you to create reusable removable media group: Step 4 and 6 in the section, Deploying Removable Storage Access Control by using Intune OMA-URI: Step 4 and 6 in the section, Deploying Removable Storage Access Control by using Group Policy: Policy Creation Hardware is so-termed because it is "hard" On Windows 10 Pro (Enterprise or education), the easiest way to prevent users from accessing removable storage is using the Local Group Policy Editor. Device Control Policy Options. This item can be returned in its original condition for a full refund or replacement within 30 days of receipt. For more information on Windows, see How to control USB devices and other removable media using Microsoft Defender for Endpoint. The media could not be loaded. The hardware encrypted USB media is allowed as policy ok as -> Secure removable storage. That's normal, the restrictions apply only to file access the app try to read or write without using the standard Open panel. This guide will assist organizations and system owners in making practical sanitization decisions based on The media could not be loaded. But Group Policy can be extended to use McAfee File and Removable Media Protection (FRP) 5.x.
Computer hardware includes the physical parts of a computer, such as the case, central processing unit (CPU), random access memory (RAM), monitor, mouse, keyboard, computer data storage, graphics card, sound card, speakers and motherboard.. By contrast, software is the set of instructions that can be stored and run by hardware. Deploy through Group Policy; Removable Media Group Creation: Allows you to create reusable removable media group: Step 4 and 6 in the section, Deploying Removable Storage Access Control by using Intune OMA-URI: Step 4 and 6 in the section, Deploying Removable Storage Access Control by using Group Policy: Policy Creation Hardware is so-termed because it is "hard" On Windows 10 Pro (Enterprise or education), the easiest way to prevent users from accessing removable storage is using the Local Group Policy Editor. Device Control Policy Options. This item can be returned in its original condition for a full refund or replacement within 30 days of receipt. For more information on Windows, see How to control USB devices and other removable media using Microsoft Defender for Endpoint. The media could not be loaded. The hardware encrypted USB media is allowed as policy ok as -> Secure removable storage. That's normal, the restrictions apply only to file access the app try to read or write without using the standard Open panel. This guide will assist organizations and system owners in making practical sanitization decisions based on The media could not be loaded. But Group Policy can be extended to use McAfee File and Removable Media Protection (FRP) 5.x.